Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Presidential inauguration ceremonies represent the cornerstone of American democratic transition, drawing global attention and creating complex security challenges that demand sophisticated, multi-layered protective measures. This analysis examines the evolution of inauguration security through the lens of historical precedents, emerging threats, and contemporary protective strategies. Specifically, it focuses on the potential range of threats facing the inauguration of President Donald J. Trump. Further examining why the Trump inauguration may have been moved indoors, this analysis suggests that suicide drone attacks, multi-cell gunmen and sniper attacks as well as the precedent set by the Mumbai attacks of 2008 might all be playing a critical role in terms of threatening the Trump inauguration’s safety and may have played critical roles in moving it indoors.
The security landscape surrounding major political events has transformed dramatically over the past two decades. The 2008 Mumbai attacks serve as a watershed moment in understanding coordinated urban warfare tactics by non-state actors. In Mumbai, ten attackers effectively paralyzed a city of millions through carefully planned, simultaneous strikes against multiple targets. The attackers demonstrated sophisticated command and control capabilities, utilizing real-time communications to adjust their tactics based on security force responses.
The Mumbai model revealed critical vulnerabilities in traditional security approaches. The attackers’ use of basic weapons combined with excellent communications and local knowledge created an asymmetric advantage that initially overwhelmed response capabilities. Security forces found themselves reactive rather than proactive, struggling to establish a coherent operational picture as multiple crisis points emerged simultaneously.
Contemporary security planners have internalized these lessons, fundamentally restructuring response protocols. Modern inauguration security architecture, like that being used to mitigate the threats facing the Trump inauguration, now incorporates dedicated tactical response teams positioned at strategic intervals, supported by overlapping surveillance coverage and redundant communication networks. These teams maintain independent operational capability while remaining integrated into the larger security framework, allowing for both localized rapid response and coordinated large-scale operations.
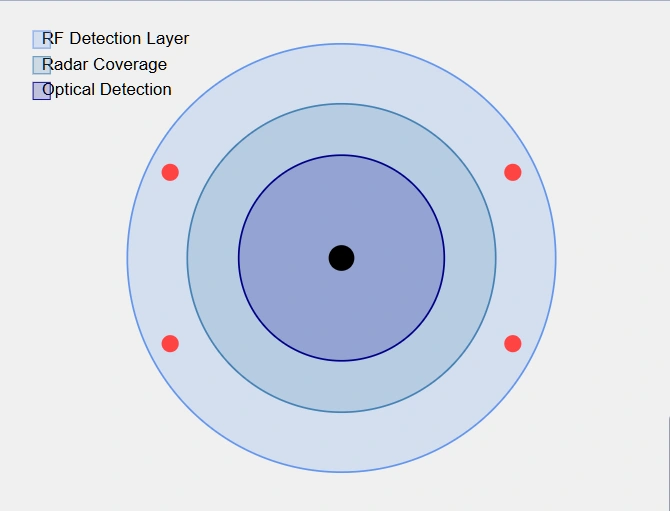
The proliferation of commercial and modified civilian drone technology has introduced unprecedented security challenges to protective operations. The tactical evolution of drone warfare in Syria and Iraq between 2014 and 2017 demonstrated how non-state actors could rapidly adapt commercial technology for military purposes. ISIS forces effectively utilized modified commercial drones for both reconnaissance and attack missions, often incorporating commercially available cameras and release mechanisms to deliver small explosive payloads. The precedents set by Russian and Ukrainian forces in the ongoing War in Ukraine, where suicide drones have been used to great effect at the tactical, operational and strategic levels, further demonstrate the manner by which drones can be repurposed for offensive purposes.
Modern inauguration security must contend with multiple drone-related threats. The availability of sophisticated commercial drone swarm technology, originally developed for light shows and industrial applications, presents particular challenges. These systems can coordinate multiple aerial platforms through single control interfaces, potentially overwhelming traditional counter-drone measures designed for individual threats.
Current counter-drone capabilities incorporate multiple detection and interdiction layers. Radio frequency detection systems scan for drone control signals and video feeds, while radar systems optimized for small aerial targets provide overlapping coverage. Advanced optical systems, including both traditional cameras and infrared sensors, complete the detection triangle. This multi-sensor approach helps mitigate the limitations of any single detection method. The potential of a primary strike using suicide drones to target the Trump Inauguration may represent one of the reasons why the event has been moved indoors in the context of insufficient domestic anti-drone systems in the capitol region – especially considering the large and mobile perimeter associated with inauguration festivities.
The targeting of first responders through secondary attacks represents a particularly challenging security consideration. This methodology gained prominence in conflict zones like Iraq and Afghanistan, where sophisticated IED networks would target initial responders to maximize casualties and disrupt emergency response capabilities. The tactic has since been adopted by various actors globally, appearing in attack planning documents and terrorist manuals.
The 2013 Boston Marathon bombing investigation revealed that the attackers had initially planned to incorporate secondary devices targeting first responders, though this aspect of their plan was not ultimately executed. Similarly, the 2019 Christchurch attacker’s manifesto and planning documents indicated intended secondary targeting of response forces, demonstrating the persistent appeal of this tactic to attackers seeking maximum impact.
Modern inauguration security planning explicitly accounts for this threat through multiple innovations in emergency response protocols. Medical response teams now operate under dedicated security elements, while casualty collection points are hardened and pre-screened. Multiple evacuation routes are established and secured in advance, with redundant options maintained throughout the event. Perhaps most importantly, response protocols now incorporate lessons from combat medicine, emphasizing the need to operate effectively under potential secondary attack conditions.
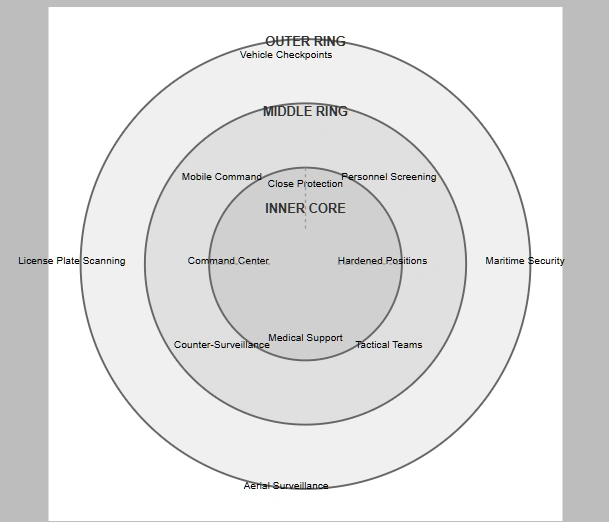
Contemporary inauguration security architecture represents one of the most sophisticated protective operations implemented in civilian environments. The system employs a defense-in-depth strategy incorporating multiple security layers, each designed to complement and reinforce adjacent protective measures while maintaining independent operational capability.
The outermost security perimeter extends well beyond the immediate event space, incorporating both physical and electronic security measures. Vehicle screening checkpoints establish initial control over ground approaches, utilizing a combination of physical inspections and technological screening methods. Advanced license plate recognition systems cross-reference vehicle information against multiple databases, while behavioral detection teams operate throughout the outer ring to identify potential surveillance or hostile reconnaissance activities.
Maritime security elements play a crucial role in outer ring security, particularly given Washington DC’s waterfront exposure. Coast Guard assets maintain exclusion zones on the Potomac River, while underwater detection systems monitor for subsurface threats. This maritime security layer coordinates closely with air defense assets to maintain comprehensive domain awareness over all approach vectors.
The middle security ring represents the critical integration zone where multiple security elements converge. Personnel screening points utilize layered inspection protocols, incorporating both traditional physical screening and advanced detection technologies. These screening points are designed with substantial queue space inside protected areas, preventing the formation of vulnerable crowds outside the security perimeter.
Tactical response teams maintain strategic positions throughout the middle ring, equipped and trained for immediate response to various threat scenarios. These teams operate under a unified command structure while maintaining the capability for independent action if communications are disrupted. Counter-surveillance units actively monitor for hostile reconnaissance, while mobile command posts provide localized command and control capabilities.
The inner security core encompasses the immediate event space and principal protection zones. This area features hardened positions designed to resist various forms of attack while maintaining the ceremonial appearance appropriate to inaugural events. Close protection teams operate within this zone under specialized protocols developed for large-scale public events, significantly different from standard VIP protection procedures.
Emergency evacuation routes from the inner core are pre-established and regularly updated based on evolving security assessments. Multiple primary and alternate routes are maintained, with dedicated security elements assigned to each. Medical support units within the inner core operate from hardened facilities, with equipment and supplies pre-positioned to support extended operations without external support.
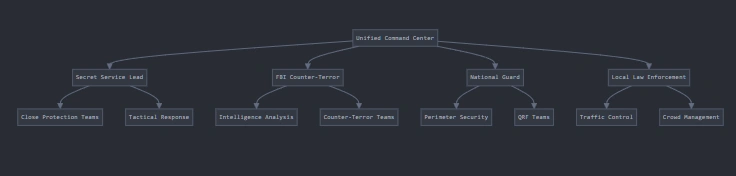
The complexity of inauguration security demands unprecedented levels of interagency coordination. The U.S. Secret Service, as the lead agency, implements a sophisticated command structure that integrates multiple federal, state, and local agencies while maintaining clear operational authority and decision-making protocols.
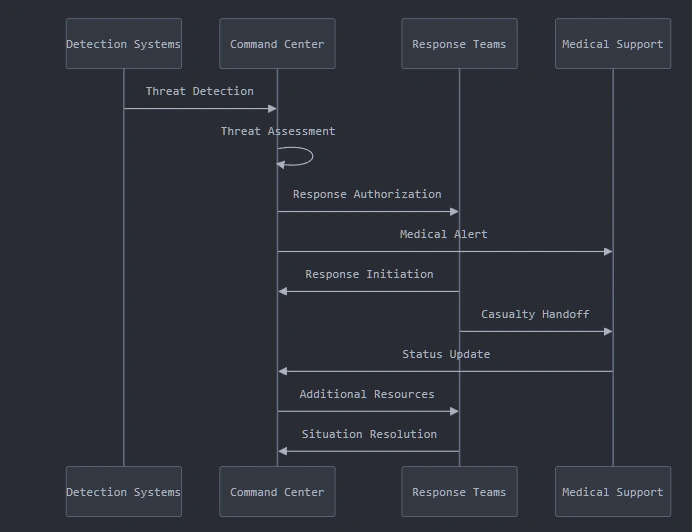
The primary command center integrates representatives from all participating agencies, providing real-time coordination capabilities across the entire security operation. Advanced communications systems ensure reliable information flow between different security elements, while dedicated tactical channels remain available for crisis response. The command infrastructure incorporates multiple redundant systems, allowing for continued operations even if primary systems are compromised.
Video integration systems provide comprehensive situational awareness, combining feeds from fixed cameras, mobile units, and aerial assets into a coherent operational picture. This integrated video network allows command elements to quickly verify reports and coordinate response actions, addressing one of the key vulnerabilities demonstrated during the Mumbai attacks.
Real-time intelligence integration represents a critical advancement in inauguration security operations. Intelligence analysts from multiple agencies work alongside operational commanders, providing immediate analysis of emerging situations. This integration allows for rapid threat assessment and response initiation, significantly reducing the decision-making timeline compared to traditional sequential assessment processes.
The FBI’s Counter-Terror Division maintains dedicated teams within the command structure, providing immediate access to national-level investigative resources and intelligence databases. These teams coordinate closely with local law enforcement intelligence units, creating a comprehensive threat detection and assessment capability that extends well beyond the immediate event perimeter.
The complexity of inauguration security creates inherent challenges in maintaining comprehensive protection while facilitating necessary public access and ceremonial functions. Modern security planning addresses these challenges through sophisticated vulnerability analysis and layered mitigation strategies.
The urban environment of Washington DC presents unique security challenges, particularly in terms of aerial and electronic security measures. The city’s street layout and building density create numerous potential blind spots in surveillance coverage, while the concentration of communications infrastructure can interfere with detection systems and tactical communications.
Counter-drone operations face particular challenges in the urban environment. Buildings create complex radar shadows that can mask approaching aerial threats, while the dense electromagnetic environment complicates electronic detection systems. Security planners address these vulnerabilities through overlapping detection systems and multiple redundant sensor types, ensuring that weaknesses in any single detection method are covered by alternative systems.
The potential for mass casualty events drives sophisticated medical response planning. Multiple casualty collection points are established throughout the security zones, each designed to operate independently if isolation becomes necessary. These facilities maintain dedicated security elements and hardened communications systems, allowing for continued operation even under developing threat conditions.
Medical response teams operate under modified protocols developed from combat medicine experience. These protocols emphasize the need to maintain operational capability under potential secondary attack conditions, incorporating security elements directly into medical response planning. Multiple evacuation routes are pre-designated for each collection point, with alternate routes and methods maintained throughout the event.
The command and control infrastructure incorporates multiple layers of communications redundancy, addressing vulnerabilities demonstrated in previous crisis events. Primary communications systems operate across multiple frequency bands and transmission methods, while backup systems utilize independent infrastructure to ensure continued operation if primary systems are compromised.
Tactical teams maintain independent communications capabilities, allowing for continued operation even if central command systems are disrupted. These systems incorporate advanced encryption and frequency-hopping technologies to resist interference and interception, while maintaining simplicity of operation under stress conditions.
The rapid evolution of technology creates both new security challenges and enhanced protective capabilities. Security planners must continuously adapt to emerging threats while leveraging technological advances to improve protective measures.
Next-generation counter-drone systems incorporate artificial intelligence for threat identification and response coordination. These systems can distinguish between authorized and unauthorized aerial platforms while maintaining the capability to respond to multiple simultaneous threats. Integration of advanced electronic warfare capabilities provides multiple options for drone interdiction, ranging from control signal disruption to direct electronic system engagement.
Machine learning systems are increasingly integrated into security operations, particularly in the realm of behavioral detection and pattern recognition. These systems analyze multiple data streams in real-time, identifying potential threat indicators that might escape human observation. Integration of AI capabilities with traditional security measures creates a more robust detection and assessment capability.
Future medical response planning increasingly emphasizes integration of civilian and tactical medical capabilities. This integration allows for more efficient resource utilization while maintaining necessary security protocols. Advanced telemedicine capabilities provide immediate access to specialized medical expertise, while new evacuation technologies improve casualty movement capabilities in challenging environments.
Based on analysis of current capabilities and emerging threats, several areas present opportunities for security enhancement.
Development of more sophisticated integration systems would improve coordination between different security elements. Enhanced real-time video analysis capabilities, combined with improved artificial intelligence support for decision-making, could reduce response times while improving accuracy of threat assessment. Implementation of advanced communications systems would enhance reliability while reducing vulnerability to interference or disruption.
Increased emphasis on response force protection represents a critical area for improvement. Enhanced armor and protective equipment for medical and security personnel, combined with improved tactical communications capabilities, would increase operational effectiveness under threat conditions. Development of more sophisticated venue hardening technologies would improve protection while maintaining necessary public access.
Better integration of emerging technologies into existing security frameworks would enhance overall protective capabilities. Advanced sensor systems, improved artificial intelligence applications, and enhanced communications technologies offer significant potential for security improvement. Implementation of these technologies must balance enhanced capability against operational complexity and reliability requirements.
Modern inauguration security represents a sophisticated integration of multiple protective elements, creating a defense-in-depth system capable of addressing various threat scenarios. The evolving threat environment demands continuous adaptation of security measures, while maintaining the delicate balance between effective protection and public access.
Future security planning must continue to evolve, incorporating new technologies and methodologies while maintaining proven protective principles. The challenge lies in enhancing security capabilities while preserving the fundamental character of inauguration ceremonies as public celebrations of democratic transition. Success requires careful integration of multiple security elements, supported by sophisticated command and control systems and comprehensive response planning.