Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

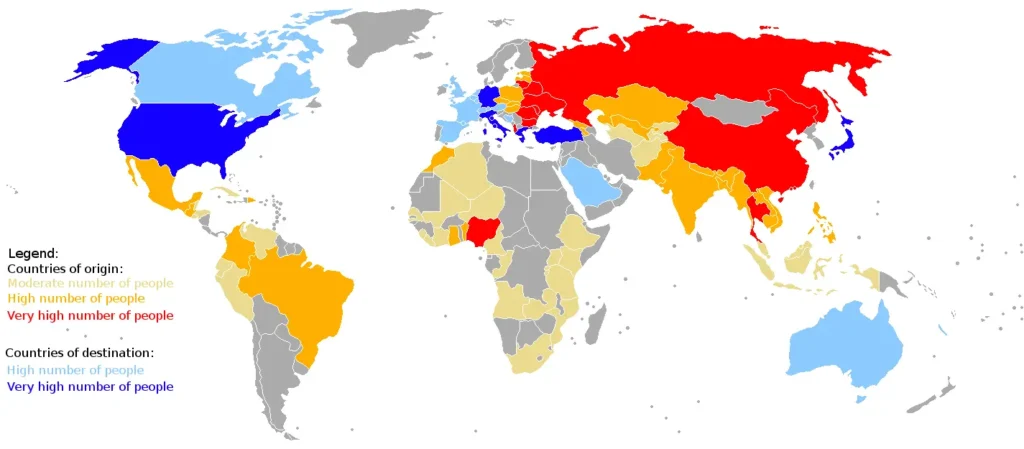
Human trafficking remains one of the most pressing and hidden crimes of our time, with traffickers increasingly exploiting digital tools to conduct and conceal their operations. From coded messages on social media to clandestine signals embedded within mapping platforms, traffickers continue to adapt to evolving technologies. A recent viral discovery on Google Maps in Los Angeles, where the words “HELP” and “TRAFICO” were spotted near a railroad yard, has ignited public speculation and concern about potential trafficking activity in the area. While the authenticity of such messages is still under debate, the incident highlights the importance of public awareness in spotting trafficking red flags and reporting them through the appropriate channels.
In today’s hyper-connected world, the general public has become both an asset and a risk in the fight against trafficking. While citizens armed with open-source intelligence (OSINT) tools can aid investigations, misinformation and sensationalism can often cloud genuine efforts to help victims. Understanding how to differentiate between credible signs of trafficking and potential hoaxes is crucial for ensuring that law enforcement and advocacy organizations can focus on real threats.
This article delves into the key indicators of human trafficking, examines how traffickers use online platforms to operate under the radar, and provides practical steps to take when encountering suspicious activity. Whether you are a concerned citizen, an OSINT investigator, or a journalist covering trafficking-related issues, recognizing and responding appropriately to trafficking signals can help combat this pervasive crime.

As digital platforms have become integral to modern life, traffickers have found new ways to exploit them to recruit, advertise, and control victims. Websites and social media platforms that offer anonymity and global reach are particularly attractive to traffickers seeking to connect with potential buyers and conceal their operations from authorities. Additionally, mapping services such as Google Maps have emerged as unexpected tools traffickers may use to leave coded signals, as some believe to be the case with the “HELP” messages found in Los Angeles – a city that is a human trafficking hotspot.
Research has shown that traffickers often create hidden signals in plain sight, using vague language, emojis, and geographic markers to communicate with each other or alert victims to meeting points. Platforms like Craigslist, Facebook, and Instagram have been used to post seemingly innocent job listings that, upon closer inspection, reveal coercive and exploitative elements. Similarly, encrypted messaging apps such as WhatsApp and Telegram have enabled traffickers to maintain control over victims while evading traditional law enforcement tactics.
The rapid spread of information, combined with the challenges of verifying sources, has made it increasingly difficult to distinguish between genuine trafficking-related content and misinformation. Cases of false alarms, where well-intentioned individuals misinterpret social media posts or mapping anomalies, have further complicated the landscape of human trafficking investigations. However, there are several consistent red flags that, when identified correctly, can help determine if online activity is linked to trafficking operations.
Human trafficking, by nature, involves coercion, deception, and control over vulnerable individuals. Online platforms serve as a medium for traffickers to recruit victims, communicate with buyers, and establish covert networks. Several common red flags can help identify potential trafficking activities, including:
One of the most prevalent indicators is vague job postings promising high salaries with minimal effort. These listings, often found on social media and classified ad websites, frequently target young individuals and those facing economic hardships. Common elements of these postings include a lack of verifiable company information, pressure for immediate responses, and requests for personal details or travel arrangements under unclear terms. Victims recruited through such job offers are often lured into forced labor or sexual exploitation under the guise of legitimate employment.
Social media platforms often harbor suspicious profiles that exhibit behaviors consistent with trafficking patterns. For instance, traffickers may use fake profiles to approach potential victims, offering them opportunities or friendships that rapidly escalate into controlling relationships. Telltale signs of such profiles include overly generic or stolen photos, inconsistent posting histories, and direct messaging that seeks to isolate individuals from their support systems.
Another alarming trend involves hidden messages within public forums, images, or mapping services. These messages may include coded language, symbols, or specific phrases used by traffickers to communicate with one another or with victims. The recent discovery of “HELP” messages on Google Maps has sparked concerns that traffickers could be using geolocation tools to send distress signals or coordinate illicit operations without drawing direct attention. While such signs must be verified, they highlight the need for public vigilance in identifying and reporting unusual patterns in the digital space.
Additionally, abrupt changes in social media behavior can indicate that someone is being controlled or manipulated. Victims of trafficking may suddenly delete their online presence, show signs of isolation, or post content that appears scripted or coerced. Such behavioral changes can be warning signs that an individual is being exploited, and it is crucial for concerned friends or family members to take action by reporting these changes to authorities or trusted organizations. It is also important to note that serious disasters like the ongoing California wildfire can also increase human trafficking dangers.
Identifying potential trafficking activity is only the first step; taking responsible and effective action is critical to ensuring victim safety and supporting ongoing investigations. When encountering possible trafficking red flags online, individuals should follow specific protocols to report their findings without jeopardizing victim safety or interfering with law enforcement efforts.
The most effective course of action is to report suspicions to official channels, such as national human trafficking hotlines, local law enforcement, or specialized organizations that focus on victim assistance. In the United States, the National Human Trafficking Hotline (1-888-373-7888) provides confidential and 24/7 support for reporting concerns and connecting with appropriate resources. Internationally, various NGOs and government agencies work to combat trafficking and offer reporting mechanisms tailored to specific regions.
For individuals engaged in OSINT investigations, it is essential to ensure that findings are verified and credible before sharing them with the public. Posting unverified claims or sharing potentially sensitive information online can do more harm than good, potentially alerting traffickers or causing unnecessary panic. Instead, compiling evidence through screenshots, metadata analysis, and pattern recognition can provide law enforcement with actionable intelligence to pursue further investigation.
Another important aspect of reporting is understanding the legal and ethical boundaries involved in citizen investigations. While it is commendable to want to help victims, engaging in unauthorized surveillance or direct confrontation with suspected traffickers can put individuals at risk and compromise ongoing cases. Working with trained professionals and advocacy organizations ensures that reports are handled appropriately and with the necessary expertise.
Open-Source Intelligence (OSINT) plays an increasingly vital role in identifying and combating human trafficking. Investigators, journalists, and digital activists use OSINT techniques to gather intelligence on human trafficking networks, identify patterns, and contribute to evidence collection for law enforcement. Tools such as social media analysis platforms, geolocation services, and sentiment monitoring tools provide valuable insights that can help uncover trafficking operations hidden within the digital landscape.
For example, satellite imagery tools like Google Earth and Sentinel Hub allow investigators to monitor suspicious locations over time, detecting changes that may indicate trafficking activity. Similarly, social media listening tools such as TweetDeck and CrowdTangle enable researchers to track conversations, hashtags, and trends related to trafficking in real time.
By leveraging OSINT techniques, individuals and organizations can contribute to the global fight against trafficking while ensuring that their efforts align with ethical standards and legal frameworks. Collaboration with NGOs, law enforcement, and policy makers can further enhance the impact of OSINT-driven initiatives, leading to tangible results in victim recovery and perpetrator prosecution.
With the rise of the internet and social media, human traffickers have adapted their tactics to exploit these digital platforms for recruitment, control, and communication. Many victims of trafficking are lured in through platforms such as Facebook, Instagram, and even professional networking sites like LinkedIn. These platforms provide traffickers with easy access to vulnerable individuals through deceptive job offers, modeling opportunities, and false promises of a better life.
For example, reports from organizations combating human trafficking have revealed that traffickers frequently disguise themselves as talent scouts, business owners, or romantic partners to gain the trust of their victims. Once trust is established, the traffickers begin to exert control over their targets through threats, coercion, and isolation tactics. In many cases, victims are stripped of their digital autonomy, with traffickers monitoring their online activity and using digital tools to exert psychological pressure.
Beyond social media, traffickers also take advantage of dark web forums and encrypted messaging apps such as Telegram and Signal. These platforms provide a level of anonymity that allows traffickers to communicate with buyers and other criminals without fear of detection. Law enforcement agencies have developed advanced OSINT techniques to infiltrate these hidden networks and track illegal activities. However, traffickers continue to evolve, employing sophisticated encryption and evasion tactics to stay ahead of investigators.
The gig economy has also contributed to new opportunities for traffickers. Platforms such as Craigslist and gig work apps provide traffickers with an easy way to advertise forced labor and exploit victims under the guise of legitimate work. Reports have shown that traffickers often post job listings for positions such as domestic work, agricultural labor, and even supposed “modeling gigs,” targeting individuals in financial distress.
Recognizing the signs of trafficking requires a keen eye and an understanding of traffickers’ common strategies. Some of the key indicators that someone may be a victim of trafficking include sudden changes in their online presence, such as deleting social media accounts, posting scripted messages, or displaying signs of emotional distress.
Another common sign is the use of specific hashtags or emojis that serve as covert signals among traffickers and buyers. Investigators have identified patterns in the use of certain emojis, such as roses, money bags, and crown symbols, to indicate the availability of trafficking victims. These seemingly innocent symbols can serve as coded messages that signal illicit activities to those in the know.
In some cases, victims of trafficking may attempt to signal for help through their online activity. They might post cryptic messages, sudden location check-ins at unfamiliar places, or share distressing content that hints at their situation. Being able to recognize these subtle calls for help can make a significant difference in identifying and assisting victims.
Technology companies have a crucial role to play in combating human trafficking online. Social media giants like Meta (formerly Facebook), TikTok, and Twitter have faced increasing pressure to address the spread of trafficking-related content on their platforms. In response, many have implemented AI-driven monitoring systems to detect suspicious activity, block harmful content, and collaborate with law enforcement agencies.
Google, for instance, has developed initiatives aimed at preventing exploitation by providing educational resources and partnering with organizations that work to combat trafficking. Efforts such as Google’s Safe Search filters help to restrict access to explicit content and prevent traffickers from exploiting search engine algorithms to reach potential buyers.
However, the challenge remains significant, as traffickers are constantly evolving their tactics to bypass detection measures. Critics argue that tech companies must do more to proactively address trafficking content by increasing transparency, improving reporting mechanisms, and investing in human moderation alongside automated systems.
If you come across potential trafficking-related content online, it’s important to follow the correct procedures to ensure that your report is effective and does not put victims at greater risk.
Do:
Don’t:
Over the years, several high-profile cases have demonstrated how online platforms can serve as both a tool for traffickers and a means for law enforcement and civilians to expose their operations. One such case is the infamous Backpage.com scandal, where the classified ad website was found to be a hub for sex trafficking, particularly involving minors. Law enforcement agencies, working in collaboration with advocacy organizations, successfully shut down the website and brought those responsible to justice.
Another notable case involves the widespread use of social media influencers as recruiters for trafficking networks. In several documented instances, traffickers have used influencers to lure victims by showcasing lavish lifestyles and offering opportunities that seem too good to be true. Investigative journalists and OSINT experts have played a critical role in exposing these schemes and raising public awareness about the dangers of online recruitment.
Open-Source Intelligence (OSINT) offers powerful tools for identifying and combating human trafficking. By analyzing publicly available data from social media, mapping services, and online marketplaces, OSINT investigators can uncover patterns that point to trafficking operations. Techniques such as reverse image searches, metadata extraction, and geolocation analysis enable investigators to piece together critical information that can assist law enforcement efforts.
For example, OSINT specialists can track the movement of suspected traffickers by analyzing satellite imagery and matching it with known trafficking routes. They can also monitor changes in social media activity, looking for shifts in language patterns or sudden removals of profiles that might indicate a trafficking situation.
Human trafficking is a complex and evolving crime that thrives in the digital age. While cases like the “HELP” messages found in Los Angeles may not always point to actual trafficking activity, they serve as important reminders of the vigilance required to combat exploitation online. Recognizing the signs of trafficking, reporting suspicious activity responsibly, and leveraging technology and OSINT techniques can make a tangible difference in the fight against modern slavery.
As awareness grows and more individuals become equipped with the knowledge to spot red flags, the hope is that traffickers will find it increasingly difficult to operate under the radar. Whether you are an investigator, advocate, or concerned citizen, staying informed and taking thoughtful action is the key to making the online world a safer place for all.