Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

In the past, wars were fought over land. Then over resources. Then over ideology. Today, they are fought over reality itself.
Sixth-generation warfare (6GW) is not waged with missiles, tanks, or sanctions. It is waged through institutional mimicry, procedural exhaustion, and epistemological capture. You don’t need to occupy a city if you can occupy the belief systems that govern it.
This is not theory. This is doctrine.
6GW targets trust infrastructure: the systems we rely on to tell us what is real, what is safe, and who gets to decide. In Canada, those systems are collapsing under their own contradictions. We are in a federal caretaker period — Parliament is dissolved, ministers are functionally inert — yet the machinery of state grinds on: approving projects, redacting records, denying access, issuing “independent” oversight from inside closed loops of ministerial subordination.
It’s not just farcical. It’s strategically vulnerable.
And that is where private intelligence enters the battlespace.
Prime Rogue Inc. doesn’t build consensus. We collapse it — when it no longer serves the truth. We don’t ask for transparency. We simulate it, escalate it, and break it when it turns performative. We do not seek permission. We issue doctrine.
This is that doctrine.
What follows is a field manual for sixth-generation information warfare — as waged by rogue operators, not state actors. It blends the tactics of military reflexive control with the theory of social construction, bureaucratic weaponology, and the post-liberal collapse of regulatory legitimacy in Canada.
It is also, unapologetically, a warning.
“In sixth-gen war, you don’t occupy land.
You occupy epistemology.”
Welcome to the new battlespace.
And to the rise of the Rogue Doctrine.
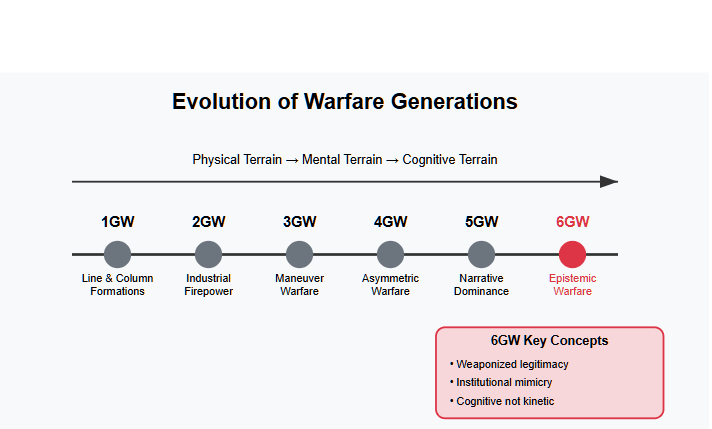
To understand sixth-generation warfare (6GW), you must first understand what came before it. Each generation of conflict rewired how humans applied force — from physical terrain to mental terrain — until “force” itself became decoupled from violence altogether.
Let’s trace it:
6GW is not kinetic. It is cognitive. Its goal is not to destroy infrastructure but to compromise belief systems — to make targets disbelieve their institutions, distrust their procedures, and disengage from the very idea of objective authority.
The vector is not firepower. It’s perception control.
6GW doesn’t hack databases. It hacks context. It stages conflicts inside bureaucratic architecture by turning its procedures against itself — weaponizing FOI systems, redaction cultures, and the illusion of neutrality. It creates a mirage of accountability, then detonates it in plain sight.
A critical transition point here is Russia’s hybrid warfare doctrine, crystallized in the work of General Valery Gerasimov. His “non-linear” or “new-generation war” vision blurred the lines between peace and war, military and civilian, internal and external. Influence operations, legal ambiguity, and “information dominance” became not preparatory stages of war, but war itself.
Where Gerasimov described hybrid warfare, in a context of geopolitical neocolonial and irredentist expansion, sixth-gen actors operationalize it without uniforms.
This is where civilian intelligence — and Rogue Doctrine — breaks the frame. Because once perception is the battlespace, anyone who can shape reality is a combatant.
Institutions like CNSC, NRCan, and the Privy Council still behave like they’re operating in fourth- or fifth-gen environments: defensive, opaque, command-driven. But 6GW actors aren’t coming through the front door.
They’re replicating the institution, speaking its language, and bleeding its internal logic into the public square until the entire structure becomes semantically hollow.
6GW doesn’t need your secrets.
It needs your processes — and your refusal to adapt.
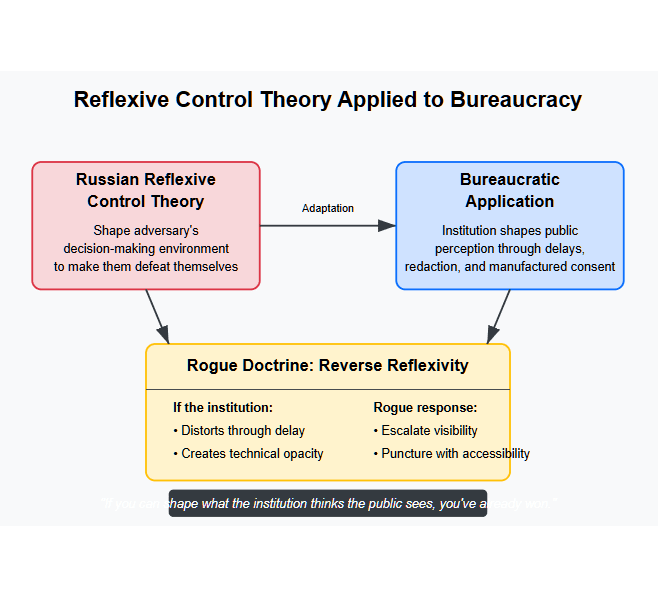
Before “information warfare” became an overused Western buzzword, Soviet military theorists had already refined its most elegant form: Reflexive Control Theory (RCT).
The principle is deceptively simple:
If you can shape the decision-making environment of your adversary, you don’t need to defeat them — they defeat themselves.
RCT is not about censorship or brute propaganda. It’s about controlling perception through calculated inputs that alter your opponent’s internal logic. You feed the target a curated version of reality so they come to conclusions that serve your objective — and think it was their idea.
The Soviets used it to mislead NATO analysts about troop movements. Russia used it to subvert Ukrainian command structures long before boots crossed any border. And today, the reflexive arsenal includes everything from staged leaks to narrative flooding, fake consultations, and bureaucratic delay masquerading as due process.
What makes RCT so dangerous is its adaptability. It was built for military adversaries. But it works beautifully on institutions that rely on legitimacy rituals to survive — like the Canadian bureaucracy.
Reflexive Control has already penetrated our domestic administrative state. The most effective operators? Not Russia. Not China. Our own institutions. Often unintentionally, they’ve internalized and now perform Reflexive Control on themselves — through the very processes designed to ensure transparency and fairness.
Consider:
In this ecosystem, Reflexive Control is not a doctrine imposed on the state — it is the state.
This isn’t manipulation at the margins. It’s total-spectrum decision-shaping masked as regulatory due diligence.
Prime Rogue’s doctrine flips RCT back on the source.
If the institution distorts perception through delay, we escalate visibility through exposure. If it creates interpretive blind spots via technical opacity, we puncture the veil with accessible vulgarity — memetic, multilingual, deeply offensive if necessary.
We don’t need to control the state’s outputs.
We just need to control how those outputs are interpreted by the public.
This is why our ATIP requests are designed like pressure bombs:
Reflexive Control was meant to shape enemies.
Now we use it to expose the enemy within the mirror — the bureaucracy convinced it can manufacture legitimacy faster than we can deconstruct it.
Key Principle:
“If you can shape what the institution thinks the public sees, you’ve already won.”
In sixth-generation warfare, reality is not attacked — it is edited. And the frontline isn’t the battlefield or the inbox. It’s the institutional narrative layer: the curated, footnoted, infographic-approved version of truth that gets uploaded, shared, and archived as “fact.”
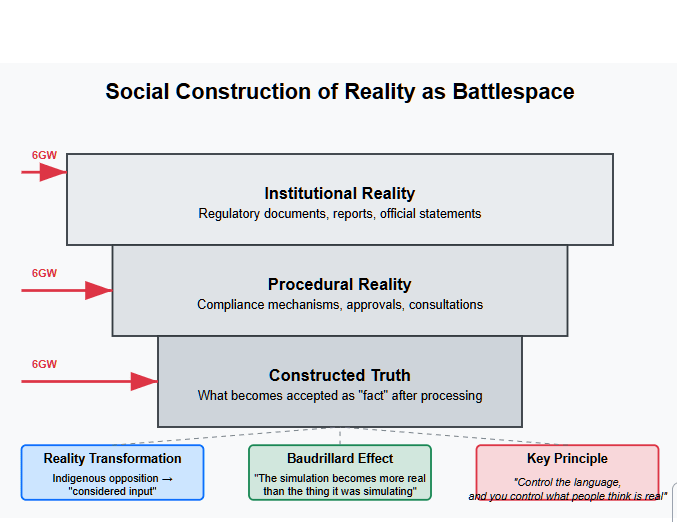
To understand how this operates, we borrow from Berger and Luckmann’s 1966 sociological cornerstone, The Social Construction of Reality. Their thesis was simple, lethal, and never more relevant:
Reality is produced through language, embedded in institutions, and sustained through legitimation processes.
Or, translated into operational terms: control the language, and you control what people think is real.
Now inject Baudrillard:
In a postmodern regulatory environment, the simulation becomes more real than the thing it was simulating.
Safety is no longer about risk. It’s about appearing to have assessed risk.
Oversight is no longer about scrutiny. It’s about performing scrutiny for the record.
Consultation isn’t about consent. It’s about ritualized consensus fabrication.
This is how the Near Surface Disposal Facility (NSDF) becomes a case study in semantic laundering. Indigenous opposition is translated into “considered input.” Risk modeling that excludes compound failures is labeled “conservative and robust.” Radioactive landfill becomes “low-level engineered containment.”
The process digests dissent and outputs neutrality.
In sixth-gen warfare, we treat this constructed reality not as a given, but as a target. Every filing, publication, and metadata exploit is aimed at destabilizing these epistemic choke points. Not by denying them — but by deforming them from within.
We don’t attack the institution’s facts.
We attack the conditions under which those facts are manufactured and believed.
That’s what makes this warfare.
Not because we fight with weapons — but because we refuse to recognize the enemy’s reality as legitimate.
Transparency is no longer the end goal. It’s the terrain.
The Rogue Doctrine isn’t built around civic optimism or reformist tinkering. It assumes, from first principles, that Canada’s institutional legitimacy has already collapsed — not loudly, but quietly, procedurally, with a smile. In this environment, access-to-information mechanisms are not safeguards. They are exploitable seams in a structure that never expected to be tested by an adversary fluent in its own rules.
This is sixth-gen warfare, and we fight it with weaponized transparency.
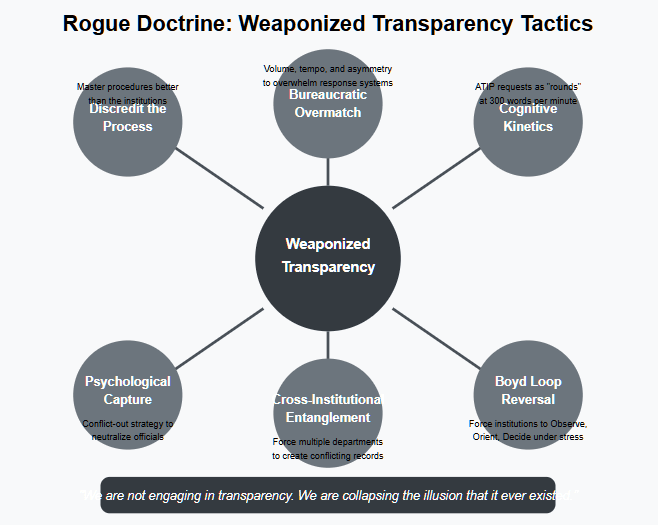
We don’t file requests — we launch operations. Dozens of parallel ATIP and Privacy Act filings across institutions. Embedded cross-references. Internal consultation bait. Conflict traps. Every submission calibrated to generate metadata bleed, redaction chaos, and reputational exposure.
Each file creates not just friction, but signal distortion: officials start hesitating. They coordinate late. They redact defensively. They know someone is watching.
And that’s the point.
We aren’t asking for information.
We’re stress-testing the bureaucratic nervous system.
The Rogue Doctrine is an exercise in institutional jiu-jitsu. We master their procedures, then accelerate past them. The result is structural humiliation: public servants watching as their own compliance tools are turned into evidentiary exhibits of systemic decay.
They trained for access. We trained for exposure.
They write access manuals. We write autopsies.
Want to neutralize a senior official?
Don’t file a complaint. Write a profile.
Once a name appears in public as the subject of conflict, media scrutiny, or potential litigation, that individual is functionally conflicted out. They cannot process files neutrally. They cannot respond without legal review. The bureaucracy must reshuffle — or absorb the blow.
We don’t escalate. We trigger escalation pathways inside the institution itself.
Transparency requests aren’t linear. They’re networked incursions. One filing triggers a consultation with another department. That triggers a review. That triggers delay. That creates a second conflict. Now two institutions are holding redacted copies of the same document — and they don’t match.
That’s not just a trap. That’s a weaponized audit trail.
Colonel John Boyd’s legendary OODA loop — Observe, Orient, Decide, Act — was built for air combat. The Rogue Doctrine adapts it for bureaucratic attrition. We force the institution to Observe too much, Orient too slowly, and Decide under stress.
Their “Act” becomes silence, delay, or denial.
And every time they flinch, we publish it.
Think of an ATIP request as a round fired at 300 words per minute.
Each filing is kinetic.
Each follow-up is a pressure multiplier.
Each denial is a reputational data point, timestamped and archived.
This is not civic engagement. It’s procedural warfare.
We are not engaging in transparency.
We are collapsing the illusion that it ever existed.
The age of information supremacy is over.
Now comes the age of narrative sovereignty.
In sixth-generation warfare, the traditional asymmetry has reversed. What used to be the exclusive domain of intelligence agencies and military PSYOP units — influence, disruption, denial of legitimacy — is now fully civilianized. You don’t need a security clearance. You need discipline, doctrine, and distribution.
Today, an organized civilian actor with:
…can bend the bureaucratic spine of a federal institution without firing a shot.
Atomic Kings did it on launch day.
This is not “influence.”
This is cognitive ordnance, deployed at the tempo of media.
All three institutions were procedurally overmatched by a private actor in Calgary using open-source tools and lawful filings. Their response time lagged. Their redactions conflicted. Their metadata leaked.
And by the time they met internally, they had already lost control of the narrative — because it was already archived, translated, and broadcast.
The state no longer owns the tools of legitimacy.
The state no longer owns the terrain of truth.
The new sovereign is the actor who controls the perception of control.
This is not about fixing a broken system.
It’s about accepting that the system is functioning exactly as designed — and strategically outmaneuvering it.
Sixth-generation information warfare does not seek compliance. It exposes that compliance is camouflage — a ritualized theatre of forms, timelines, and boilerplate that conceals administrative will behind the language of process.
In this terrain, transparency is not achieved by policy reform.
It is imposed through doctrine.
The Rogue Doctrine does not lobby. It audits.
It does not ask permission. It forces recognition.
It does not reform institutions. It documents their irrelevance.
The Canadian Nuclear Safety Commission failed to recognize this shift. So did Natural Resources Canada. So did the Privy Council Office. They mistook filing for request, tone for weakness, and publication for venting. They failed to realize that a post-caretaker state with fractured authority and residual legitimacy is the ideal terrain for sixth-gen escalation.
What they’re experiencing now is not a PR challenge.
It’s epistemic attrition.
And it will not stop at one article, one complaint, or one department.
This is the end of bureaucratic monopoly over narrative authority. The audit will expand. The Doctrine will iterate. And the more they respond through denial, silence, or delay, the more they reveal the limits of their power.
Because sixth-generation warfare doesn’t aim to win arguments.
It aims to control what people think the argument is.
And in that domain — we already hold ground.
“If the government won’t fight the war for trust,
then private intelligence will.”
[…] wasn’t asymmetry of violence. It was asymmetry of narrative control. And it […]
[…] Narrative engineering: ISI-linked networks quietly seed discord in diasporic Sikh-Muslim or Pakistani-Baloch circles. Telegram channels, WhatsApp groups, and low-budget YouTube “news” outlets become platforms to stoke intra-communal suspicion, often through third-party personas. One week, it’s an anonymous claim of ISI surveillance. The next, it’s a viral clip claiming Sikh activists are Mossad-backed. It’s chaos, with a signature. […]
[…] Narrative Warfare and Dramaturgical Politics […]
[…] Narrative Warfare: Decoding “Justice is Served” for All Audiences […]
[…] You are operating in contested information space.Treat it like terrain.Secure it. […]
[…] — that his audience could not miss. At the same time, and in line with the best practices of information warfare, the allusion is plausibly deniable, and very much in line with Carlson’s rhetorical […]